Infosec Reading List - September 2019
On a monthly basis I will publish my reading recommendations which mainly focus on Information Security (InfoSec) and Outdoor Sports. All InfoSec Reading Lists can be found here. Text in italic represent quotes from the original article.
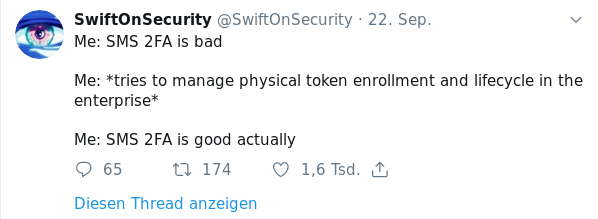
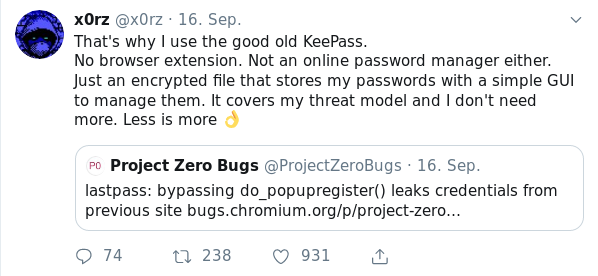
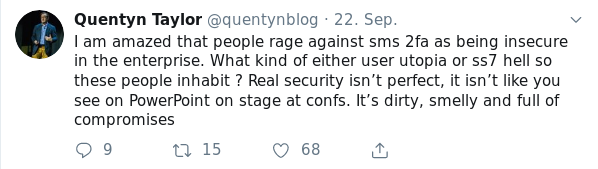
Quotes from the Twitterverse
InfoSec
- JSON and Common Web Encodings Demystified - [link]
- How to steal a million (of your data) - “After all, it’s convenient when passwords and bank card details are autofilled in the required fields. But we recommend against entrusting such vital information to browsers, since the methods of protection they use are no obstacle to malware.” - think about password manager extensions for browsers - I somehow dislike them, while respecting their value-add to usability - [link]
- Face recognition and AI ethics - fascinating article that I really enjoyed reading, it demystifies all that drama around AI a little bit - “We worried that these databases would contain bad data or bad assumptions, and in particular that they might inadvertently and unconsciously encode the existing prejudices and biases of our societies and fix them into machinery. We worried people would screw up. And, we worried about people deliberately building and using these systems to do bad things.” - [link]
- Banks, Arbitrary Password Restrictions and Why They Don’t Matter - “judging banks by the same measures we judge basic authentication schemes is an apples and oranges comparison” - “So wrapping it all up in reverse order, arbitrary low limits on length and character composition are bad. They look bad, they lead to negative speculation about security posture and they break tools like password managers.” - [link]
- Asus, Lenovo and Other Routers Riddled with Remotely Exploitable Bugs - [link]
- Covert Keylogging: Sniping your Typing - [link]
- VirusTotal for Investigators - [pdf] an extensive 150 pages document that explains the details around how to use VirusTotal for more detailed investigations - [link]
- Search Engine for ippsec youtube videos - [link]
- Real-Time Monitoring and Notifications using Shodan - [link]
- Introduction to modern network load balancing and proxying - long and great article where I really learned a lot about the various considerations for doing proper load balancing - [link]
- Day 63: Top 10 Essential NMAP Scripts for Web App Hacking - [link]
- Interview With the Guy Who Tried to Frame Me for Heroin Possession - interesting article, also recommend to review the PDF linked at the bottom - [link]
- Researchers Say They Uncovered Uzbekistan Hacking Operations Due to Spectacularly Bad OPSEC - a rather funny story about nation-state actors that are also make mistakes like all other humans - “… installing Kaspersky’s antivirus software on machines it uses to write new malware, allowing Kaspersky to detect and grab malicious code still in development before it’s deployed;” - “The group’s mistakes led Kaspersky to discover four zero-day exploits SandCat had purchased from third-party brokers to target victim machines, effectively rendering those exploits ineffective.” - [link]
- Mariposa Botnet Author, Darkcode Crime Forum Admin Arrested in Germany - [link]
- Connect Box CH7465LG: Unauthenticated Remote Code Execution (CVE-2019-13025) - rather bad: “Although the web interface is protected by a password, most of the APIs do not require any form of authentication.” - [link]
- The South American Power Outage That Plunged 48 Million Into Blackout - [link]
- A malicious website can infect my iPhone. Fact or fiction? - [link]
- Issue 1943: Signal: Incoming call can be connected without user interaction - sounds rather bad - important is to put it into the right perspective: “Worth noting that it was Android only, your phone would ring, display as a connected call, and log the completed call at the top of your conversation list. It’s not silently “enabling the microphone.” Also fixed.” - [link]
- Looking back at the Snowden revelations - excellent summary with some parts that we should keep very strongly in our minds years after the revelations since various of these topics haven’t left the global discussion table yet: “Just to make everything a bit more horrifying, Juniper’s Dual EC backdoor would later be hijacked and turned against the United States by unknown hackers illustrating exactly how reckless this all was.” … “This means that we, here in the West, had better get our stuff together or else we should be prepared to get a taste of our own medicine.” - [link]
Outdoor
- Trans Himalaya 2019: Breathless in the Himalaya - “This Darwinistic, ‘must conquer at all costs’ mindset put people in danger.” - [link]
- Fear serves a purpose. It keeps us safe. - If we never step outside of that zone, we never truly know what we are capable of. And, bloody hell, are you capable of some amazing stuff … - [link]
- Australian bushwalker rescued after crawling for two days with leg ‘clean snapped in half’ - “Parker, who is an experienced guide with Brisbane Bushwalkers, used hiking sticks to splint his leg and then spent two days crawling back to a clearing.” - [link]
- Packrafting List of Tips - [DE] - [link]
This post is licensed under CC BY 4.0 by the author.