Infosec Reading List - May 2019
On a monthly basis I will publish my reading recommendations which mainly focus on Information Security (InfoSec) and Outdoor Sports. All InfoSec Reading Lists can be found here. Text in italic represent quotes from the original article.
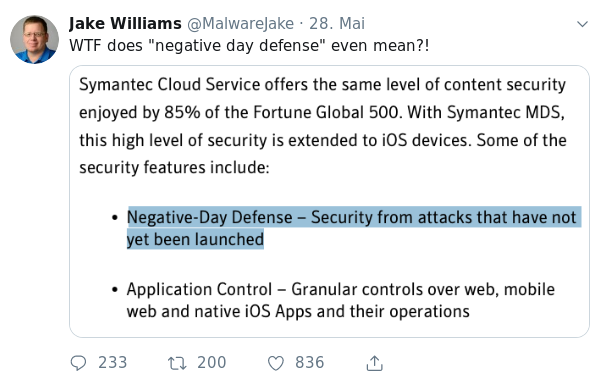
Quotes from the Twitterverse
InfoSec
- Amazon Workers Are Listening to What You Tell Alexa - this situation is a great demonstration that the artificial intelligence is not yet that artificial: The team comprises a mix of contractors and full-time Amazon employees who work in outposts from Boston to Costa Rica, India and Romania, according to the people, who signed nondisclosure agreements barring them from speaking publicly about the program. They work nine hours a day, with each reviewer parsing as many as 1,000 audio clips per shift, according to two workers based at Amazon’s Bucharest office - [link]
- Hackers Hijacked ASUS Software Updates to Install Backdoors on Thousands of Computers - I’d say this attack stands out from previous ones while being one level up in complexity and stealthiness. The filtering of targets in a surgical manner by their MAC addresses is one of the reasons it stayed undetected for so long. If you are not a target, the malware is virtually silent - [link]
- NMAP Tips: RTFM? - [link]
- Why The Intercept Really Closed the Snowden Archive - [link]
- CEO of Israeli spyware-maker NSO on fighting terror, Khashoggi murder, and Saudi Arabia - [link]
- Hackers Steal and Ransom Financial Data Related to Some of the World’s Largest Companies - the communication part in this incident is interesting - the affected company stated: CITYCOMP Service GmbH has successfully fended off a hacker attack and does not yield to blackmail. The repercussion is the publication of the stolen customer data. - see here - my question is: how can you talk about a “successful” defense of an attack in case the outcome is that your customer data gets published? - [link]
- How I hacked 50+ Companies in 6 hrs - server-side template injection + RCE = gameover - [link]
- Remote Code Execution on most Dell computers - [link]
- How I Eat For Free in NYC Using Python, Automation, Artificial Intelligence, and Instagram - this is an excellent example what can be done with data scientist skills and social media - it’s basically the description of creating a bot that serves a very specific purpose: getting you free meals - The best part is that it seems more human than most accounts in the same niche. - [link]
- Subdomains Enumeration - [link]
- Shodan Safari, where hackers heckle the worst devices put on the internet - “If you leave something on the internet long enough, someone will hack it.” in fact, there is no need to put everything on the Internet - [link]
- Following The RTM: Forensic Examination Of A Computer Infected With A Banking Trojan - [link]
- eyeDisk. Hacking the unhackable. Again - “So, a lot of complex SCSI commands were used to understand the controller side of the device, but obtaining the password/iris can be achieved by simply sniffing the USB traffic to get the password/hash in clear text.” - [link]
- Post-mortem and remediations for Apr 11 security incident - an extensive post-incident analysis of the matrix.org hack - this is quite rare nowadays, hence, I strongly recommend to go through the report and take some of the key lesssons learnt - a short summary I will give you below via copy&paste of the important text parts: “We also didn’t spend much time hardening the default Debian installations - for instance, the default image allows root access via SSH and allows SSH agent forwarding, and the config wasn’t tweaked.” - “So we ended up with two production environments;” - “The attacker had first compromised Jenkins on March 13th via an RCE vulnerability” - [link]
- The Difference Between Goals, Strategies, Metrics, OKRs, KPIs, and KRIs - “Metrics are measurements of things that matter to help you make better decisions.” - [link]
- 0day “In the Wild” - “Today, we’re sharing our tracking spreadsheet for publicly known cases of detected zero-day exploits, in the hope that this can be a useful community resource” - [link]
- Security by Compartmentalization: Qubes is an Open-Source OS Tackling the Most Sophisticated Modern Threats - “We do, however, find it amusing that many security experts around the world have deemed a ‘reasonably secure’ operating system to be the most secure operating system available.” - [link]
- From hard drive to over-heard drive: Boffins convert spinning rust into eavesdropping mic - “It’s not just the walls that have ears. It’s also the hard drives.” - [link]
- Faulty database script brings Salesforce to its knees - “According to reports on Reddit, users didn’t just get read access, but they also received write permissions, making it easy for malicious employees to steal or tamper with a company’s data.” - [link]
Outdoor
- Self-Rescue - [link]
- Montanas Vacias (Empty Mountains) - interesting bikepacking route in Spain - [link]
- The Case for Doing Nothing - [link]
- Cape to Cairo: 12,000km on Foot - “I started to completely lose the fear factor, the excitement. Losing fear is dangerous because you end up doing things that can get you in a lot of trouble.” - [link]
This post is licensed under CC BY 4.0 by the author.