Infosec Reading List - January 2024
On a monthly basis I will publish my reading recommendations which mainly focus on Information Security (InfoSec) and Outdoor Sports. All InfoSec Reading Lists can be found here. Text in italic represent quotes from the original article.
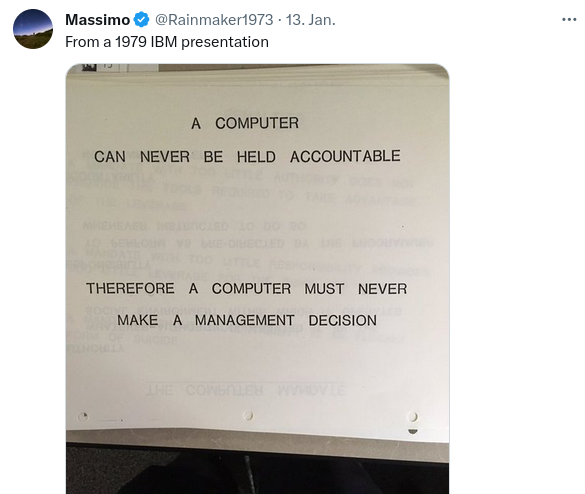
Quotes from the Twitterverse
InfoSec
- How I built a fully offline smart home, and why you should too - ask yourself the question: why should you connect your smart home network to the Internet anyway? - [link]
- A TOUCH OF PWN - PART I - Our research revealed multiple vulnerabilities that our team successfully exploited, allowing us to completely bypass Windows Hello authentication on all three laptops. - [link]
- ViziOwn – Exploiting the Vizio SmartCast Platform - Please note this post goes into detail regarding a remote code execution mechanism in a component of software common to different model TV’s, which differ in both software stack and CPU/SOC, but just happen to feature a common vulnerability. - Can I play DOOM? - [link]
- Ransomware Diaries: Volume 2 – A Ransomware Hacker Origin Story - [link]
- How to Lead Across a Siloed Organization - We now know that lateral agility is a vital capability for today’s senior leader. It’s no longer enough to lead a team well — too much work happens across functions and organizations. The very definition of effective leadership has changed in response to that reality. - [link]
- Building a fully local LLM voice assistant to control my smart home - [link]
- More companies expected to disclose email hacks by Russian intelligence - [link]
- Microsoft’s Dangerous Addiction To Security Revenue - They need to throw away this poisonous idea of security as a separate profit center and rededicate themselves to shipping products that are secure-by-default while providing all security features to all customers. - [link]
- Hacking into a Toyota/Eicher Motors insurance company by exploiting their premium calculator website - An Eicher Motors premium calculator website on a Toyota Tsusho Insurance Broker India subdomain exposed Microsoft corporate cloud credentials. - [link]
- Quantum Computing’s Hard, Cold Reality Check Hype is everywhere, skeptics say, and practical applications are still far away - The quantum computer revolution may be further off and more limited than many have been led to believe. That’s the message coming from a small but vocal set of prominent skeptics in and around the emerging quantum computing industry. - The conclusion, says Troyer, was that quantum computers will only really shine on small-data problems with exponential speed ups. “All the rest is beautiful theory, but will not be practical,” he adds. - [link]
- PLAYING WITH FIRE – HOW WE EXECUTED A CRITICAL SUPPLY CHAIN ATTACK ON PYTORCH - [link]
- The 10,000-Hour Rule is a Myth - The most common misunderstanding of the 10,000-hour rule was the assumption that time spent simply using the skill was what ultimately mattered. - [link]
- 3 Opportunities for Cybersecurity Leaders Who Choose to Stay - Keep at it,Slow it down, or Accelerate. - [link]
- The unlikely 3 million electric toothbrush DDoS attack - [link]
Outdoor
N/A
This post is licensed under CC BY 4.0 by the author.