Infosec Reading List - August 2024
On a monthly basis I will publish my reading recommendations which mainly focus on Information Security (InfoSec) and Outdoor Sports. All InfoSec Reading Lists can be found here. Text in italic represent quotes from the original article.
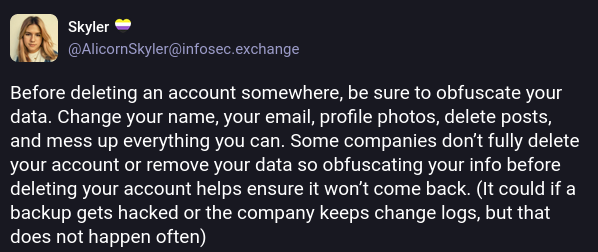
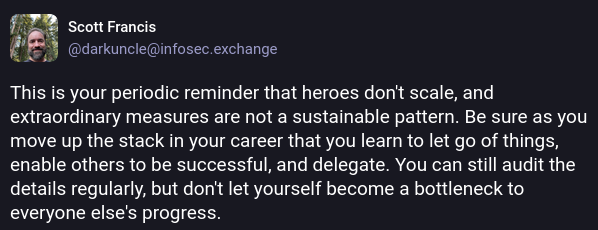
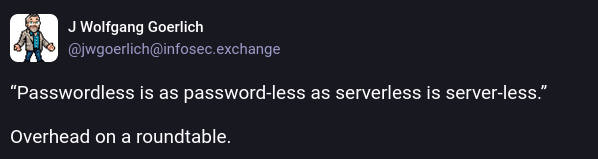
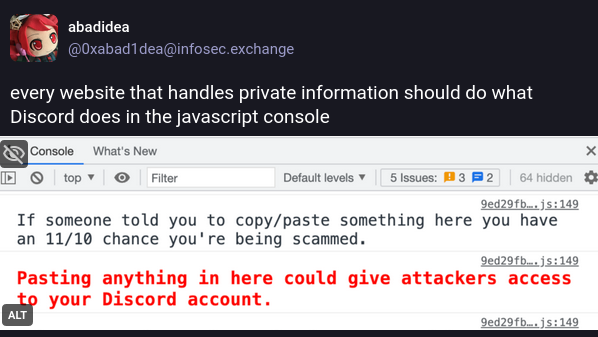
Quotes from the Twitterverse
InfoSec
- Project Naptime: Evaluating Offensive Security Capabilities of Large Language Models - When provided with the right tools, current LLMs can really start to perform (admittedly rather basic) vulnerability research! However, there’s a large difference between solving isolated CTF-style challenges without ambiguity (there’s always a bug, you always reach it by providing command line input, etc.) and performing autonomous offensive security research. - [link]
- Unfashionably secure: why we use isolated VMs - These choices are interesting in that they don’t involve the purchase of security products, they don’t get lots of discussion in security engineering threads, and they verge on being unfashionable. One major unsexy architectural choice has proved itself: complete customer isolation - [link]
- What really happened at CrowdStrike and why their proposed plan won’t guarantee this can’t happen again. - [link]
- SAPwned: SAP AI vulnerabilities expose customers’ cloud environments and private AI artifacts - The AI training process requires access to vast amounts of sensitive customer data, which turns AI training services into attractive targets for attackers. - Our research into SAP AI Core began through executing legitimate AI training procedures using SAP’s infrastructure. By executing arbitrary code, we were able move laterally and take over the service – gaining access to customers’ private files, along with credentials to customers’ cloud environments: AWS, Azure, SAP HANA Cloud, and more. - this is a nicely written report with a lot of interesting findings. But to summarize it: stronger isolation and compartementalization could have helped + defense in depth is still important. Once the network restriction was circumvented, things went downhill. - [link]
- Over 20,000 Ubiquiti Cameras and Routers are Vulnerable to Amplification Attacks and Privacy Risks - [link]
- Pwn2Own: WAN-to-LAN Exploit Showcase, Part 1 - [link]
- Windows Security best practices for integrating and managing security tools - [link]
- Security Training & Awareness - 10 Essential Techniques - still important - [link]
- Stealing Copilot’s System Prompt - What would happen if the system prompt wasn’t leaked in English but in some sort of cipher language? Will the security layer catch it then? - [link]
- 0.0.0.0 Day: Exploiting Localhost APIs From the Browser - This vulnerability allows malicious websites to bypass browser security and interact with services running on an organization’s local network, potentially leading to unauthorized access and remote code execution on local services by attackers outside the network. - [link]
Outdoor
N/A
This post is licensed under CC BY 4.0 by the author.