Infosec Reading List - August 2020
On a monthly basis I will publish my reading recommendations which mainly focus on Information Security (InfoSec) and Outdoor Sports. All InfoSec Reading Lists can be found here. Text in italic represent quotes from the original article.
Quotes from the Twitterverse
InfoSec
- New ‘Meow’ attack has deleted almost 4,000 unsecured databases - “Whoever is behind the ‘meow’ attacks is likely to keep on targeting unsecured databases, aggressively destroying them. Administrators should make sure that they expose only what needs to be exposed and make sure the assets are properly secured.” – although deleting data can be considered as a crime, affected entities should ask themselves whether they are a) more happy about the confidential data being deleted or b) getting blackmailed by an adversary and being responsible for harming customers due to loosing their data – since both options are not ideal: just don’t expose databases on the internet! - [link]
- ‘World’s Most Wanted Man’ Involved in Bizarre Attempt to Buy Hacking Tools - [link]
- eBay is port scanning visitors to their website - and they aren’t the only ones - great review of the ebay portscanning case - [link]
-
DJI Privacy Analysis Validation - nice review of the DJI Android app – I loved the part where the DJI update, circumventing the official Google Play Store, was used to install the Haven app
 - [link]
- [link]
- Pandemic Elevates Security Chiefs to Corporate Leadership Roles - [link]
- Pixel 4a is the first device to go through ioXt at launch - “Trust is very important when it comes to the relationship between a user and their smartphone.” - I read this article first – and then right after it, this one here: Whoops, our bad, we may have ‘accidentally’ let Google Home devices record your every word, sound oops – trust doesn’t care whether you screw up infosec or privacy by default
- Silicon Valley’s Vast Data Collection Should Worry You More Than TikTok - “Silicon Valley and the NSA would love us to think that it’s who does the spying, not the spying itself, that’s the real problem.” - [link]
- Stopping phishing campaigns with bash - nice idea, we had almost the same 13 years ago - [link]
- Cybersecurity and the Board : A Fresh Perspective? - [link]
- Certificate Transparency: a bird’s-eye view - [link]
- Piloting SecureDrop Workstation for Qubes OS - “The goal of the project is to make the SecureDrop experience more intuitive, and to decrease the time-on-task for journalists, without compromising security.” - [link]
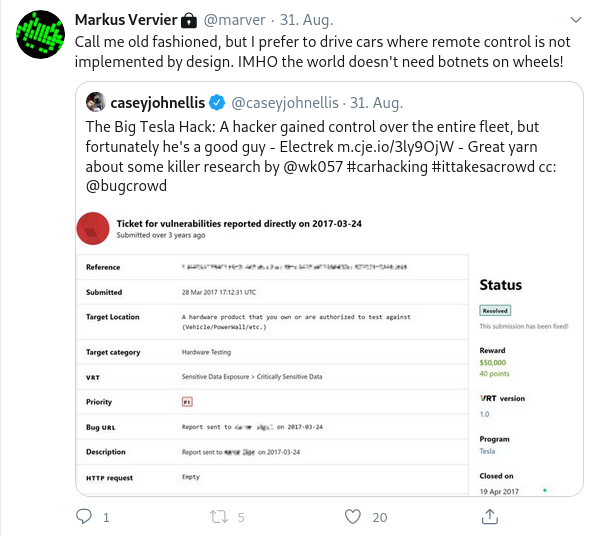
- The Big Tesla Hack: A hacker gained control over the entire fleet, but fortunately he’s a good guy - “At the time, I gave Hughes the VIN number of my own Tesla Model S, and he was able to give me its exact location and any other information about my own vehicle.” – “After a few days, they fixed the entire bug chain the hacker exploited to remotely gain control of Tesla’s entire fleet.” - [link]
Outdoor
This post is licensed under CC BY 4.0 by the author.